I found a potential data inaccuracy in Oracle's Critical Patch Update Advisory for April 2024
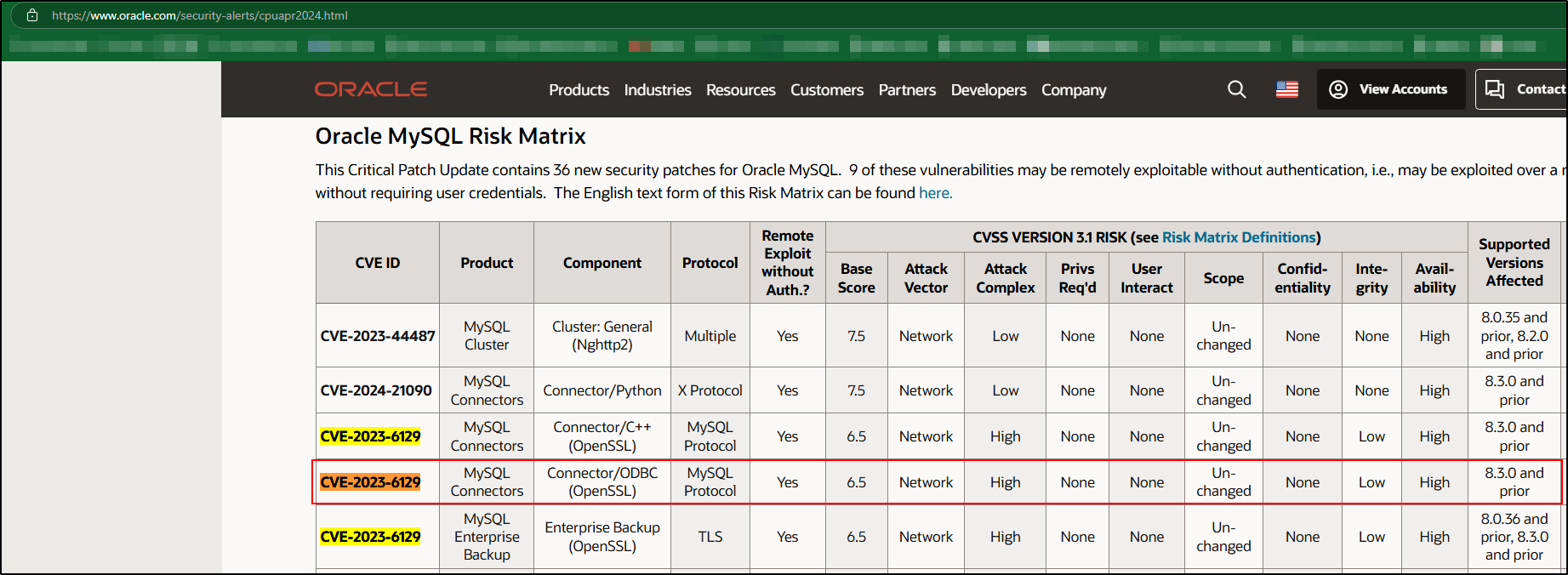
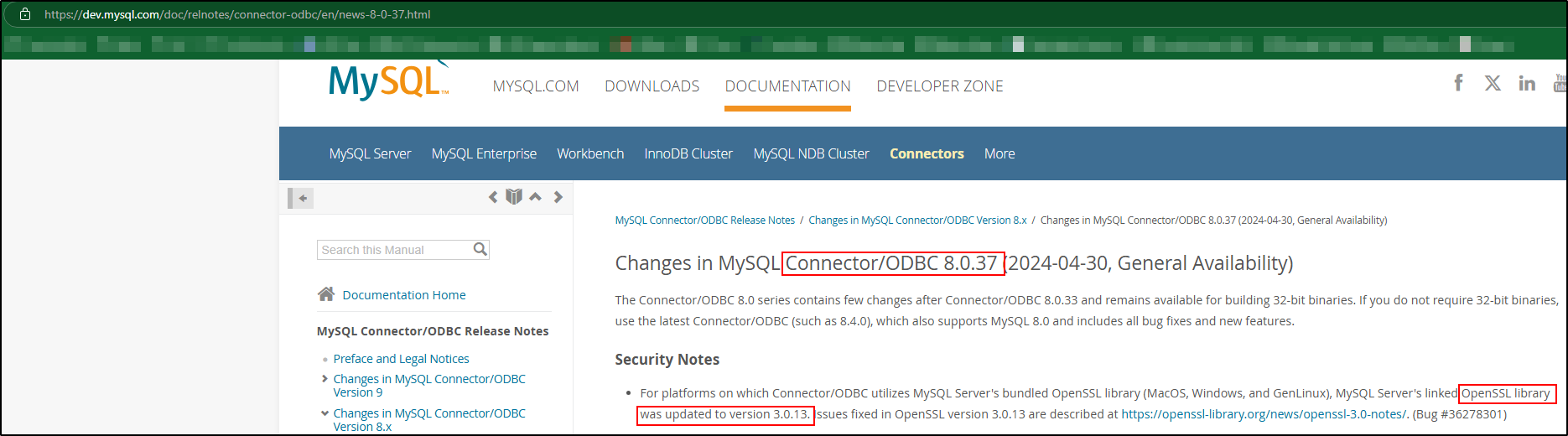
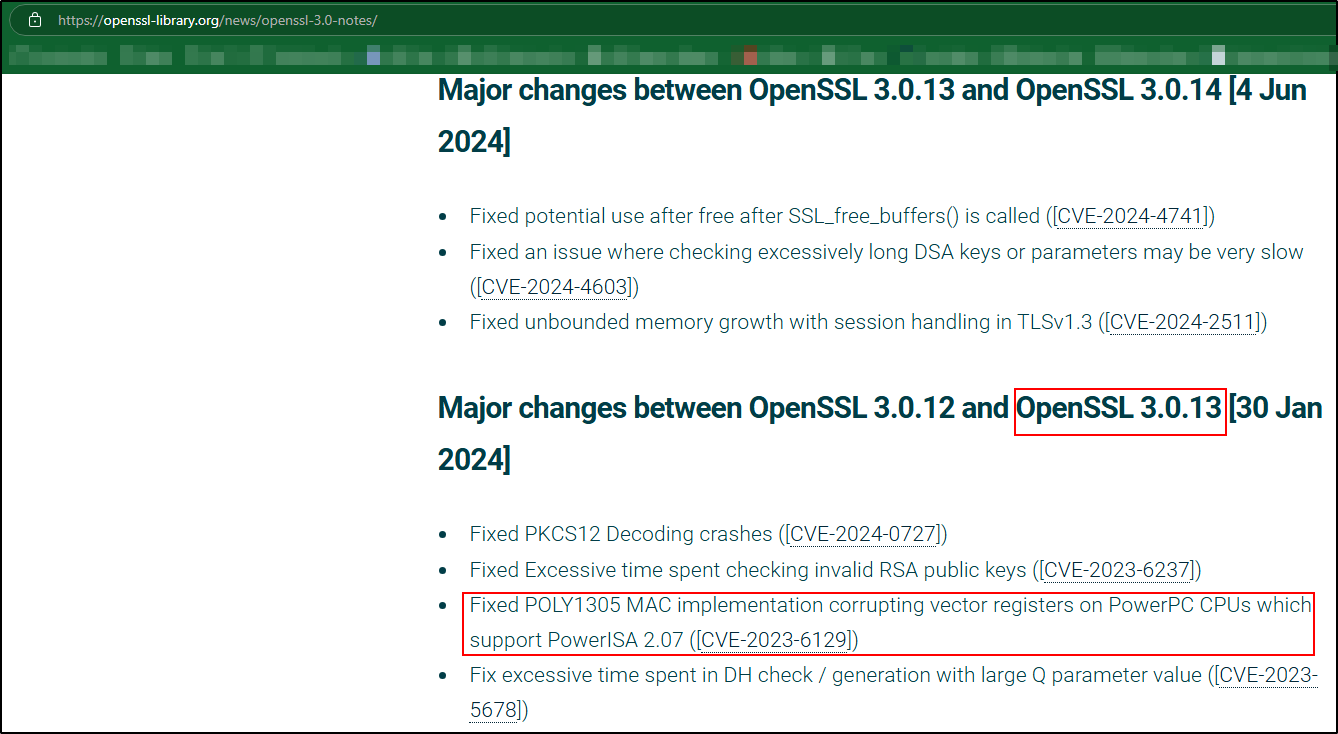
Specifically for CVE-2023-6129 on the Connector/ODBC (OpenSSL). In the risk matrix, it states that the ODBC connector is affected by the CVE in versions 8.3.0 and prior. In the release notes for the ODBC connector however, it states that as of version 8.0.37, it was patched to include the version of OpenSSL that is no longer affected by the CVE. So it looks like the line for ODBC connector should list “8.0.36 and prior, 8.3.0 and prior” as affected versions.
This is important, because scanners like Tenable will not accept the above argumentation to fix their scanner logic, they simply look at your risk matrix to determine how their scanners identify vulnerabilities, and are identifying anything that is 8.0.37 or higher as vulnerable to the CVE.
Sources:
Oracle patch advisory:
https://www.oracle.com/security-alerts/cpuapr2024.html
ODBC Connector release notes:
https://dev.mysql.com/doc/relnotes/connector-odbc/en/news-8-0-37.html
OpenSSL release notes:
https://openssl-library.org/news/openssl-3.0-notes/