Hi all,
Here the context.
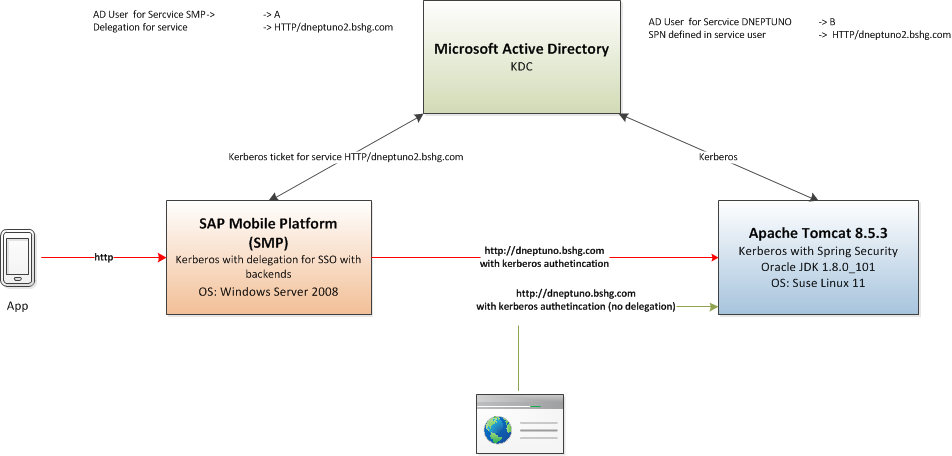
- SAP Mobile platform requests a Kerberos ticket for a service. Delegation is configured for it's service user (User A can requests tickets for a service which belongs to a different user)
- With this ticket, SMP authenticates the user against tomcat where an application is running with Spring Security (JGSS is doing the magic behind)
- When the module tries to validate the ticket, we have the exception described in detail at the end of the post
Caused by: org.ietf.jgss.GSSException**:Failure unspecified at GSS-API level (Mechanism level: No cksum in AP\_REQ'sauthenticator)**
- The funny thing is with the browser (without delegation) Kerberos is working properly.
¿Any idea about what could be causing this behavior?
Thanks in advance and best regards!
Raúl
Exception
Caused by: org.ietf.jgss.GSSException: Failure unspecified at GSS-API level (Mechanism level: No cksum in AP_REQ's authenticator)
at sun.security.jgss.krb5.InitialToken$OverloadedChecksum.<init>(InitialToken.java:220) ~[na:1.8.0_101]
at sun.security.jgss.krb5.InitSecContextToken.<init>(InitSecContextToken.java:131) ~[na:1.8.0_101]
at sun.security.jgss.krb5.Krb5Context.acceptSecContext(Krb5Context.java:829) ~[na:1.8.0_101]
at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:342) ~[na:1.8.0_101]
at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:285) ~[na:1.8.0_101]
at sun.security.jgss.spnego.SpNegoContext.GSS_acceptSecContext(SpNegoContext.java:906) ~[na:1.8.0_101]
at sun.security.jgss.spnego.SpNegoContext.acceptSecContext(SpNegoContext.java:556) ~[na:1.8.0_101]
at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:342) ~[na:1.8.0_101]
at sun.security.jgss.GSSContextImpl.acceptSecContext(GSSContextImpl.java:285) ~[na:1.8.0_101]
here debug info shown while trying to validate ticket
Found KeyTab
/neptuno/keys/keytab/dneptuno2.bshg.com.keytab for [HTTP/dneptuno2.bshg.com@EUCE.CORP.BSHG.COM](mailto:HTTP/dneptuno2.bshg.com@EUCE.CORP.BSHG.COM)
Entered Krb5Context.acceptSecContext with state=STATE_NEW
Looking for keys for: HTTP/dneptuno2.bshg.com@EUCE.CORP.BSHG.COM
Added key: 23version: 2
>>> EType:
sun.security.krb5.internal.crypto.ArcFourHmacEType
Using builtin default etypes for permitted_enctypes
default etypes for permitted_enctypes: 17 16 23.
>>> EType:
sun.security.krb5.internal.crypto.ArcFourHmacEType
MemoryCache: add 1472643443/068238/C4F3C48B35155EECCF2570E4D5EBF07E/XXXXXXXX@bshg.com@EUCE.CORP.BSHG.COM
to XXXXXXX@bshg.com@EUCE.CORP.BSHG.COM|HTTP/dneptuno2.bshg.com@EUCE.CORP.BSHG.COM
MemoryCache: Existing AuthList:
#1: 1472643107/247289/F8C26EA6D6BB2269AE800A3954A305DE/XXXXXXXX@bshg.com@EUCE.CORP.BSHG.COM
>>> KrbApReq: authenticate succeed.