Hi
Any information / blogs etc. most welcome!
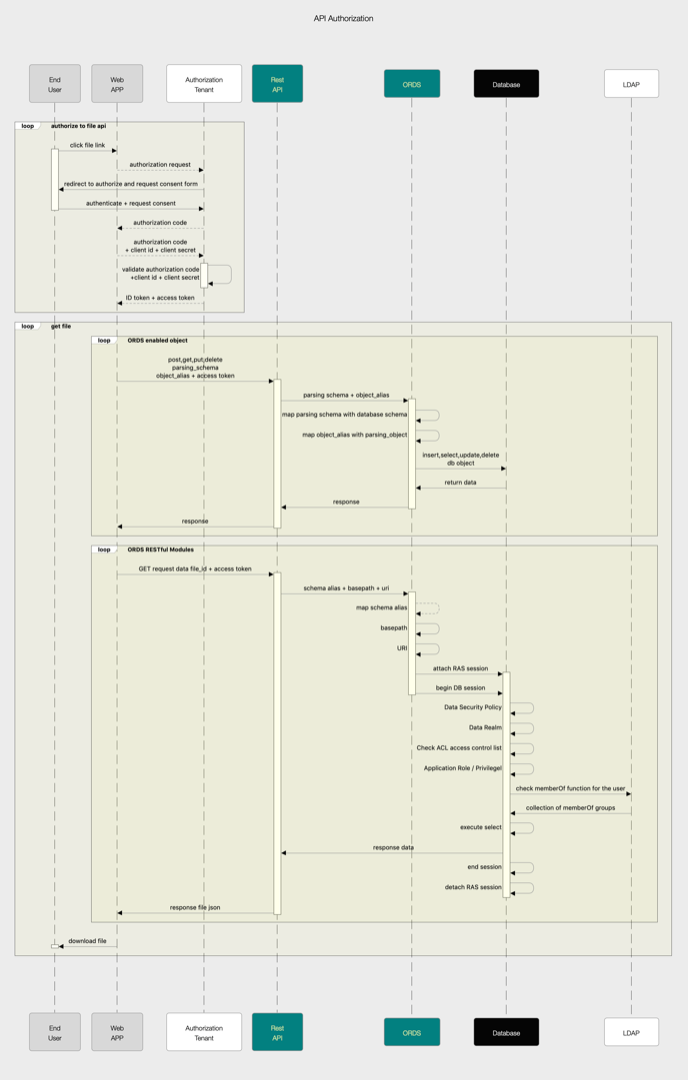
I made very harsh sequence diagram draft about fictive case where the api serves e.f. file data but expects that:
- end user consuming the api via web application can be authenticated e.g. sso
- the web application is authorized to use the api
- there is secure and transparent method to convey the end user information for the db which has ras/fgac policies constraining access to data, additional checks etc..
- there is no possibility for rebel application to harvest the api by shuffling input parameters
Please comment what could be potentially improve the sequence diagram (it surely is defective ) and also if you already know if there any best practices for creating:
- Apex web application which consumes Apex web service on top of ras-hardened db and fulfills the above criteria ...

rgrds Paavo